G1 Secure Communicator
The G1 is a closed mobile system for person to person messaging
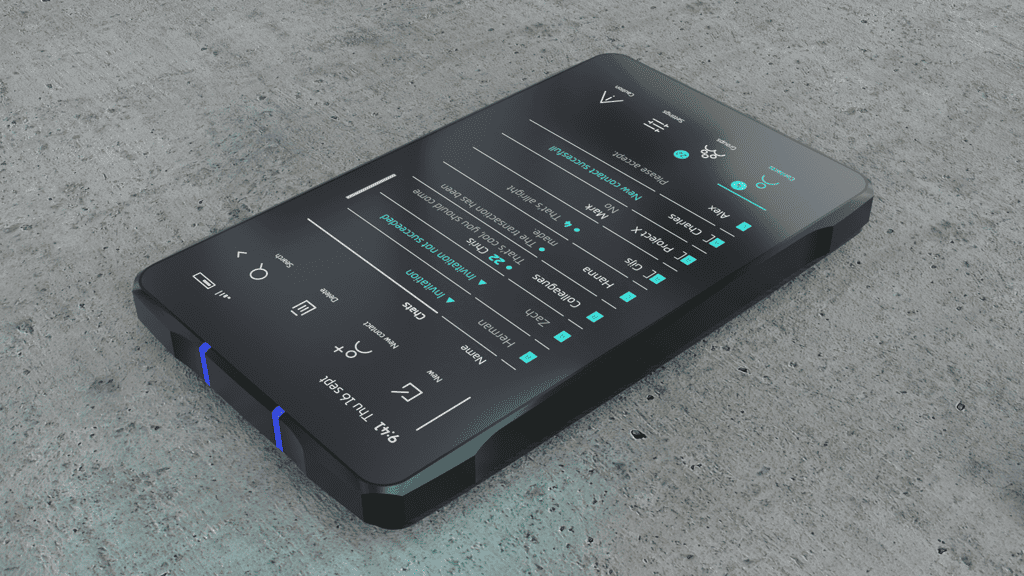
Direct Benefits
Developed for TOP SECRET level security
Our secure communications technology is designed to provide the highest safety achievable in secure communications.No infrastructure
The ARMA G1 communications system relies on Tor network, which is public infrastructure. Therefore, the purchase and maintenance of infrastructure is not needed.Seamless integration
Setting up a closed secure communications network based on the ARMA G1 requires no significant actions. Users activate the device in minutes and can easily add contacts by sharing short lived codes. ARMA can provide its clients with additional custom services.Dynamic Identity
ARMA’s patented Dynamic Identity feature prevents you from becoming a target by regularly interchanging the International Mobile Subscriber Identifier (IMSI) number, with at the heart of it ARMA’s virtual SIM that replaces a conventional physical SIM card.Serverless Infrastructure
End to end encrypted data is sent directly to its intended recipient through TOR, a public network, that anonymously routes user data through several random and encrypted relay servers across the globe. Messaging servers are not used at all. This leaves no infrastructure or persistent data to attack.
OS ARMA Linux
Chipset ARMA
CPU Arm i.MX8M
RAM 1 GB
Internal storage 16 GB
SIM
ARMA virtual SIM OS
ARMA Dynamic IdentityModem U-Blox Global Use
LTE FDD
Bands: 1, 2, 3, 4, 5, 7, 8, 18, 19, 20, 3, 4, 5, 7, 8, 18, 19, 20, 26, 283G UMTS/HSDPA/HSUPA
Bands: 1, 2, 5, 82G GSM/GPRS/EDGE
GSM 850 Mhz
E-GSM 900 Mhz
DCS 1800 Mhz
PCS 1900 MhzType AMOLED 5.44”
Resolution 1920×1080
Input Capacitive, multi-touch
Dimensions length x width x height (mm) 114 x 85 x 15
Weight (g) 244 grams
Battery capacity (mAh) 7000
Charging Wireless
Input Touch
Material Stainless steel and Kevlar Aramid composite
Dust and water resistance IP65 and IP67
Shock resistance MIL STD 810G standard
Platform
Network
Display
Body
Dynamic Identity
ARMA’s patented Dynamic Identity feature prevents you from becoming a target by regularly interchanging the International Mobile Subscriber Identifier (IMSI) number, with at the heart of it ARMA’s virtual SIM that replaces a conventional physical SIM card.Serverless Infrastructure
End to end encrypted data is sent directly to its intended recipient through TOR, a public network, that anonymously routes user data through several random and encrypted relay servers across the globe. Messaging servers are not used at all. This leaves no infrastructure or persistent data to attack.Controlled ecosystem
Secure ecosystem through zero-trust policy, from hardware and operating system to software and organisation.Non-extractable keys
Encryption and decryption with non-extractable keys that are generated and stay on the device, unknown to ARMA or any third party.Isolated cellular modem
Modem is isolated from the device’s main computing core and has no direct memory access.Controlled execution environment
Trusted boot and firmware updates and cryptographic verification of the boot image integrity.Microservice architecture
Individual software components are isolated using operating system containers.Single application
Dedicated messaging, no third party applications.Passports
Multiple aliases are possible on a single device. Certain contact groups may be handled isolated and independently.Self destruct
All critical hardware components are protected in a tamper resistant enclosure. If the integrity of the device is compromised, all encryption keys are irrecoverably erased.Closed network
No interoperability with other communications systems.Anti-tamper
Tamper resistant enclosure, if compromised, all encryption keys are irrecoverably erased.TEMPEST resistant
Both passive and active measures are in place to ensure the blocking of electromagnetic emissions that otherwise would leak sensitive information.Minimal attack surface
No connectors, NFC, Bluetooth, WIFI, GPS, speaker, microphone or sensorsGovernance
Control System for Transparency provides transparency in root of trust, manufacturing, system and organisation
Unlimited global roaming
ARMA Instruments specifically has no insight into the ARMA G1’s geographical location nor the amount of data that it uses. Therefor billing per device is not possible. Subscriptions are based on a 1 year flat fee allowing for a full year of worldwide unlimited and unrestricted use of our service.Unlimited global roaming
ARMA Instruments specifically has no insight into the ARMA G1’s geographical location nor the amount of data that it uses. Therefor billing per device is not possible. Subscriptions are based on a 1 year flat fee allowing for a full year of worldwide unlimited and unrestricted use of our service.Unlimited global roaming
ARMA Instruments specifically has no insight into the ARMA G1’s geographical location nor the amount of data that it uses. Therefor billing per device is not possible. Subscriptions are based on a 1 year flat fee allowing for a full year of worldwide unlimited and unrestricted use of our service.Unlimited global roaming
ARMA Instruments specifically has no insight into the ARMA G1’s geographical location nor the amount of data that it uses. Therefor billing per device is not possible. Subscriptions are based on a 1 year flat fee allowing for a full year of worldwide unlimited and unrestricted use of our service.Threat Intelligence Center
As part of our Secure Operations Center the ARMA Threat Intelligence Center is based on the collection of intelligence using open source intelligence, social media intelligence, human Intelligence, technical intelligence or intelligence from the deep and dark web. It’s key mission is to research and analyse trends and technical developments in the areas of cybercrime, hacktivism and cyber espionage.
This enables us to anticipate, respond to and remediate threats on all levels, whether user operational, legislative, distribution or otherwise.Threat Intelligence Center
As part of our Secure Operations Center the ARMA Threat Intelligence Center is based on the collection of intelligence using open source intelligence, social media intelligence, human Intelligence, technical intelligence or intelligence from the deep and dark web. It’s key mission is to research and analyse trends and technical developments in the areas of cybercrime, hacktivism and cyber espionage.
This enables us to anticipate, respond to and remediate threats on all levels, whether user operational, legislative, distribution or otherwise.Transparency Center
Our transparency center is open to all our customers. It provides on premises tour of our facilities and has staff available to enable customers to investigate our source code, updates, operations- and threat intelligence center.Transparency Center
Our transparency center is open to all our customers. It provides on premises tour of our facilities and has staff available to enable customers to investigate our source code, updates, operations- and threat intelligence center.Customer & after sales support
Our customer service center is available 24/7 by phone and email through our contact center.
We have advanced support standby and an R&D department which handles confirmed bugs or feature requests from customers.
Depending on the customers service contract, device guarantee issues are processed under 48 hours from notification.Customer & after sales support
Our customer service center is available 24/7 by phone and email through our contact center.
We have advanced support standby and an R&D department which handles confirmed bugs or feature requests from customers.
Depending on the customers service contract, device guarantee issues are processed under 48 hours from notification.Transparency Center
Our transparency center is open to all our customers. It provides on premises tour of our facilities and has staff available to enable customers to investigate our source code, updates, operations- and threat intelligence center.Transparency Center
Our transparency center is open to all our customers. It provides on premises tour of our facilities and has staff available to enable customers to investigate our source code, updates, operations- and threat intelligence center.Customer & after sales support
Our customer service center is available 24/7 by phone and email through our contact center.
We have advanced support standby and an R&D department which handles confirmed bugs or feature requests from customers.
Depending on the customers service contract, device guarantee issues are processed under 48 hours from notification.Customer & after sales support
Our customer service center is available 24/7 by phone and email through our contact center.
We have advanced support standby and an R&D department which handles confirmed bugs or feature requests from customers.
Depending on the customers service contract, device guarantee issues are processed under 48 hours from notification.
Unlimited global roaming
ARMA Instruments specifically has no insight into the ARMA G1’s geographical location nor the amount of data that it uses. Therefor billing per device is not possible. Subscriptions are based on a 1 year flat fee allowing for a full year of worldwide unlimited and unrestricted use of our service.Unlimited global roaming
ARMA Instruments specifically has no insight into the ARMA G1’s geographical location nor the amount of data that it uses. Therefor billing per device is not possible. Subscriptions are based on a 1 year flat fee allowing for a full year of worldwide unlimited and unrestricted use of our service.Unlimited global roaming
ARMA Instruments specifically has no insight into the ARMA G1’s geographical location nor the amount of data that it uses. Therefor billing per device is not possible. Subscriptions are based on a 1 year flat fee allowing for a full year of worldwide unlimited and unrestricted use of our service.Unlimited global roaming
ARMA Instruments specifically has no insight into the ARMA G1’s geographical location nor the amount of data that it uses. Therefor billing per device is not possible. Subscriptions are based on a 1 year flat fee allowing for a full year of worldwide unlimited and unrestricted use of our service.Threat Intelligence Center
As part of our Secure Operations Center the ARMA Threat Intelligence Center is based on the collection of intelligence using open source intelligence, social media intelligence, human Intelligence, technical intelligence or intelligence from the deep and dark web. It’s key mission is to research and analyse trends and technical developments in the areas of cybercrime, hacktivism and cyber espionage.
This enables us to anticipate, respond to and remediate threats on all levels, whether user operational, legislative, distribution or otherwise.Threat Intelligence Center
As part of our Secure Operations Center the ARMA Threat Intelligence Center is based on the collection of intelligence using open source intelligence, social media intelligence, human Intelligence, technical intelligence or intelligence from the deep and dark web. It’s key mission is to research and analyse trends and technical developments in the areas of cybercrime, hacktivism and cyber espionage.
This enables us to anticipate, respond to and remediate threats on all levels, whether user operational, legislative, distribution or otherwise.Transparency Center
Our transparency center is open to all our customers. It provides on premises tour of our facilities and has staff available to enable customers to investigate our source code, updates, operations- and threat intelligence center.Transparency Center
Our transparency center is open to all our customers. It provides on premises tour of our facilities and has staff available to enable customers to investigate our source code, updates, operations- and threat intelligence center.Customer & after sales support
Our customer service center is available 24/7 by phone and email through our contact center.
We have advanced support standby and an R&D department which handles confirmed bugs or feature requests from customers.
Depending on the customers service contract, device guarantee issues are processed under 48 hours from notification.Customer & after sales support
Our customer service center is available 24/7 by phone and email through our contact center.
We have advanced support standby and an R&D department which handles confirmed bugs or feature requests from customers.
Depending on the customers service contract, device guarantee issues are processed under 48 hours from notification.Transparency Center
Our transparency center is open to all our customers. It provides on premises tour of our facilities and has staff available to enable customers to investigate our source code, updates, operations- and threat intelligence center.Transparency Center
Our transparency center is open to all our customers. It provides on premises tour of our facilities and has staff available to enable customers to investigate our source code, updates, operations- and threat intelligence center.Customer & after sales support
Our customer service center is available 24/7 by phone and email through our contact center.
We have advanced support standby and an R&D department which handles confirmed bugs or feature requests from customers.
Depending on the customers service contract, device guarantee issues are processed under 48 hours from notification.Customer & after sales support
Our customer service center is available 24/7 by phone and email through our contact center.
We have advanced support standby and an R&D department which handles confirmed bugs or feature requests from customers.
Depending on the customers service contract, device guarantee issues are processed under 48 hours from notification.